
The World Economic Forum’s annual Global Cybersecurity Outlook provides a comprehensive state-of-the-nation analysis of cyber security.
The World Economic Forum (WEF) has published its annual Cybersecurity Outlook. This report offers a detailed overview of the global cybersecurity landscape, focusing on the rising risks and growing complexity of the field. The report is based on a global survey of 321 respondents and one-on-one interviews with C-level executives from global companies.
The conclusion is simple: The growing complexity of cyberspace is an undeniable reality.
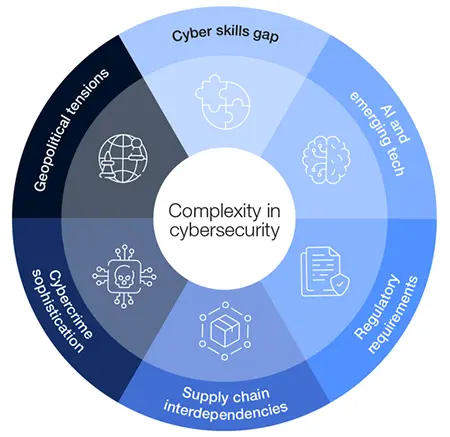
Decoding complexity from a board perspective
The basic challenge with these types of comprehensive reports is the amount of details. So many topics and potential issues are mentioned but what actions should a board member take? What areas should be prioritized? Because without focus, it’s like trying to boil the ocean, and cyber resilience will not improve.
Below are some key questions and insights based on the categories highlighted in WEF’s report. While these questions are definitely not the only questions to consider, they serve as a foundation for critical business risk discussions.
Since WEF’s report focuses mostly on cybersecurity risks, it’s natural as a board member to ask what measures should be taken to improve visibility, enhance resilience, and mitigate risks. However, we should also consider more positive views, for example what potential new business opportunities this evolving risk landscape might present.
Escalating geopolitical tensions and supply chain interdependencies
Geopolitical tensions contribute to an increasingly uncertain business environment. Nation-state actors target not only governments but also economies and critical infrastructure. These tensions naturally have an impact on supply chains. Especially growing reliance on complex supply chains connecting multiple subcontractors, countries, and continents results in a more opaque risk landscape. Geopolitical tensions and supply chain interdependencies require companies to assess risks beyond their direct control and boundaries, potentially requiring ecosystem level mitigation measures:
Relevant questions to ask:
- Ecosystem: What is our company’s position in the digital ecosystem?
- Ecosystem: What does our digital ecosystem map look like? Who are we dependent on, and who depends on us?
- Ecosystem: Have we collaborated with ecosystem partners to address these risks?
- Ecosystem: Are we or our partners potential targets of state-sponsored attacks?
- Scenarios: What are the top three worst-case business scenarios that could significantly impact operations, and how are we prepared? What would happen if partner A went down for two weeks? What have been the most severe cyber incidents in our industry over the past 12 months?
- Scenarios: Have we recently executed any tabletop exercises to test and improve our readiness and resilience? What did we learn from these exercises?
- Development: What measures have we implemented in the past year to mitigate these risks?
Cybercrime sophistication
As attacks become more advanced, companies must invest in people, processes, and technology to strengthen cyber defenses proactively. A company should compare its investments to the levels of the industry and ecosystem so that it does not become the weakest link by accident. Unfortunately, cyber criminals operate nowadays as a business and their “go-to-market strategy” prioritizes “customers” that are easy to penetrate.
Relevant questions to ask:
- Spend: What is our cyber defense budget trend, and how does it compare with industry standards?
- Spend: If we increased cyber defense spending by 10%, what additional risks could be mitigated?
- Process: What is our cyber incident data revealing? Is the trend improving because of our better visibility related to incidents (i.e. we see better) or because of a meaningful change in threat landscape (i.e. there are more threats than before)?
- People: Does our culture encourage the reporting of security anomalies?
- Scope: Are we addressing cyber risks across all domains:
- Traditional IT systems?
- Manufacturing/production systems (like factory machines)?
- Customer-facing digital products and services?
- Development: Do we have known weak spots in our cyber defense, and when are we going to address them? What’s the business rationale for our cybersecurity roadmap priorities?
- Development: Are we improving our defense and resilience fast enough or are the risks growing even faster?
- The last resort: When was the last time we reviewed our cyber insurance coverage if any?
Rapid adoption of emerging technologies
While new technologies offer substantial benefits, they also introduce new vulnerabilities that cybercriminals can exploit. Same technological advancements that can be used for defense can naturally be used for attacks by adversaries. New technology like AI can introduce vulnerabilities not only in technical systems but also in traditional human based processes.
Relevant questions to ask:
- Process: How do we assess the evolving technology landscape? Do we regularly get updates about the latest technological advancements in our business domain?
- Process: Do we have critical internal approval processes that rely on outdated verification methods (like phone calls or paper-based documents), making them vulnerable to AI-driven fraud?
- People: Does our company culture promote responsible adoption of new technologies? Do we have the means to control the use of new technology like the latest AI tools if needed?
- People / ecosystem: Do we have internal experts or external partners with the competence to understand new technologies and their impact?
Proliferation and fragmentation of regulatory requirements
The increasing number of cybersecurity regulations worldwide creates significant compliance challenges for organizations. Meeting these new requirements takes effort, money and expertise. And becoming compliant by just meeting the requirements might not be enough. Since all companies in a specific sector must comply with the same regulations, the regulatory requirements just define the new minimum level.
Relevant questions to ask:
- Ambition: Is our goal to meet or exceed regulatory requirements? Should we aim to simply meet requirements or exceed them to gain a competitive advantage?
- Process: Who is responsible for tracking regulatory developments?
- Process: Are we prepared to detect, react to, and report cyber incidents within regulatory deadlines? Have our capabilities to report on time been tested?
Widening cyber skills gap
The shortage of skilled cybersecurity professionals makes risk management increasingly difficult. Detection tools and technologies help to get new insights, but they rarely understand business relevance. Up-to-date cybersecurity expertise combined with business domain understanding is a critical combination to manage cyber risks.
Relevant questions to ask:
- Leadership: Who is responsible for cyber risk oversight, and how is this person supported by the management?
- Leadership: Can our cybersecurity leadership communicate risks and needed mitigation measures effectively in business terms?
- People: How does our cyber defense team size compare to industry standards?
- People: What is our cyber security team’s growth or attrition rate, and how does it compare with the overall industry? What is the reason behind the growth or attrition?
- People: Are our cybersecurity awareness campaigns impactful, or just compliance-driven?
- Ecosystem: Do we have partners who can provide additional expertise when needed?
Hopefully this analysis helps provide relevant discussion points and actionable insights to tackle modern cybersecurity risks.
While cybersecurity is complex and constantly evolving, we must avoid falling into the trap of overly technical language. At its core, cybersecurity is a modern business risk management issue–nothing more, nothing less.



